The high-density computational capability of RTL8762 achieves the optimal Find My solution
2023/06/15
Realtek introduces the Find My solution based on the RTL8762 series, which features strong computational capabilities and abundant RAM resources. It is highly suitable for applications that require the intensive encryption algorithms in Find My. Additionally, the RTL8762 series demonstrates outstanding performance with its ultra-low power consumption and hardware encryption algorithm support, making it an ideal fit for the Find My solution.
Apple's Find My feature allows users to locate lost items using a network composed of millions of Apple devices. By utilizing this feature, users can activate a private and secure finding function, and locate their lost items through the Find My network. The entire process is completely anonymous and protected by end-to-end encryption, ensuring maximum privacy for all users. Data is retained on Apple's servers for no longer than 24 hours, and Apple and certified third-party vendors are not able to view the location or information of the product.
Benefiting from Apple's powerful ecosystem influence, the Find My feature has rapidly proliferated across a wide range of consumer products, including key cards, headphones, luggage, bags, and scooters.

Find My workflow
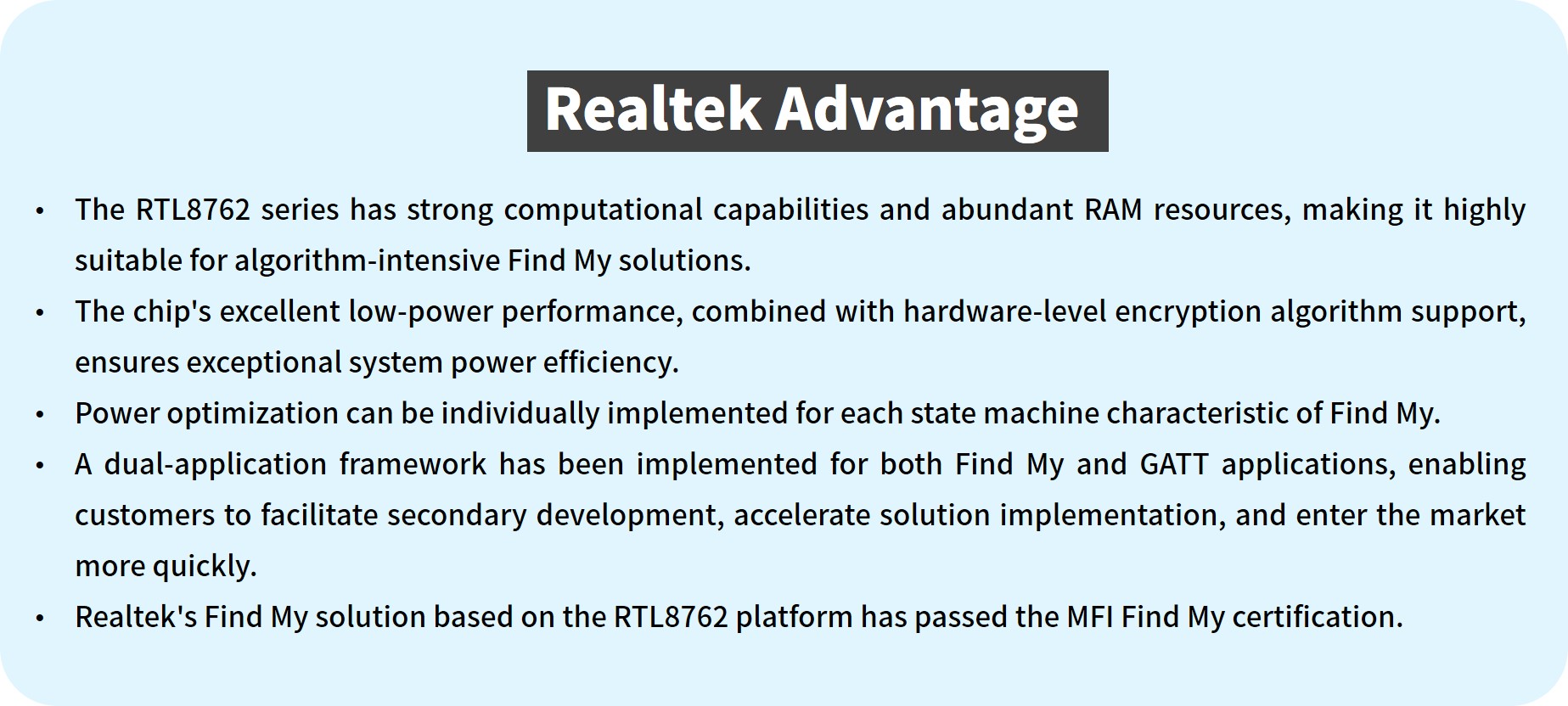
• To utilize a Find My accessory, the owner device (such as an iPhone equipped with the Find My app) needs to establish a connection and pair with the accessory. During the pairing process, a pair of keys will be negotiated, with the owner device storing the private key and public key, while the accessory retains the public key.
• As a BLE beacon, the accessory broadcasts a rotating key derived from the public key.
• Upon receiving the broadcast from the accessory, nearby Apple devices (Finder devices) send the key and their own location information encrypted with this key to Apple servers.
• After retrieving the relevant location information from the Apple servers, the owner device decrypts the location data using the private key, thereby obtaining the location information of the accessory.
Find My Application Scenario
• Position
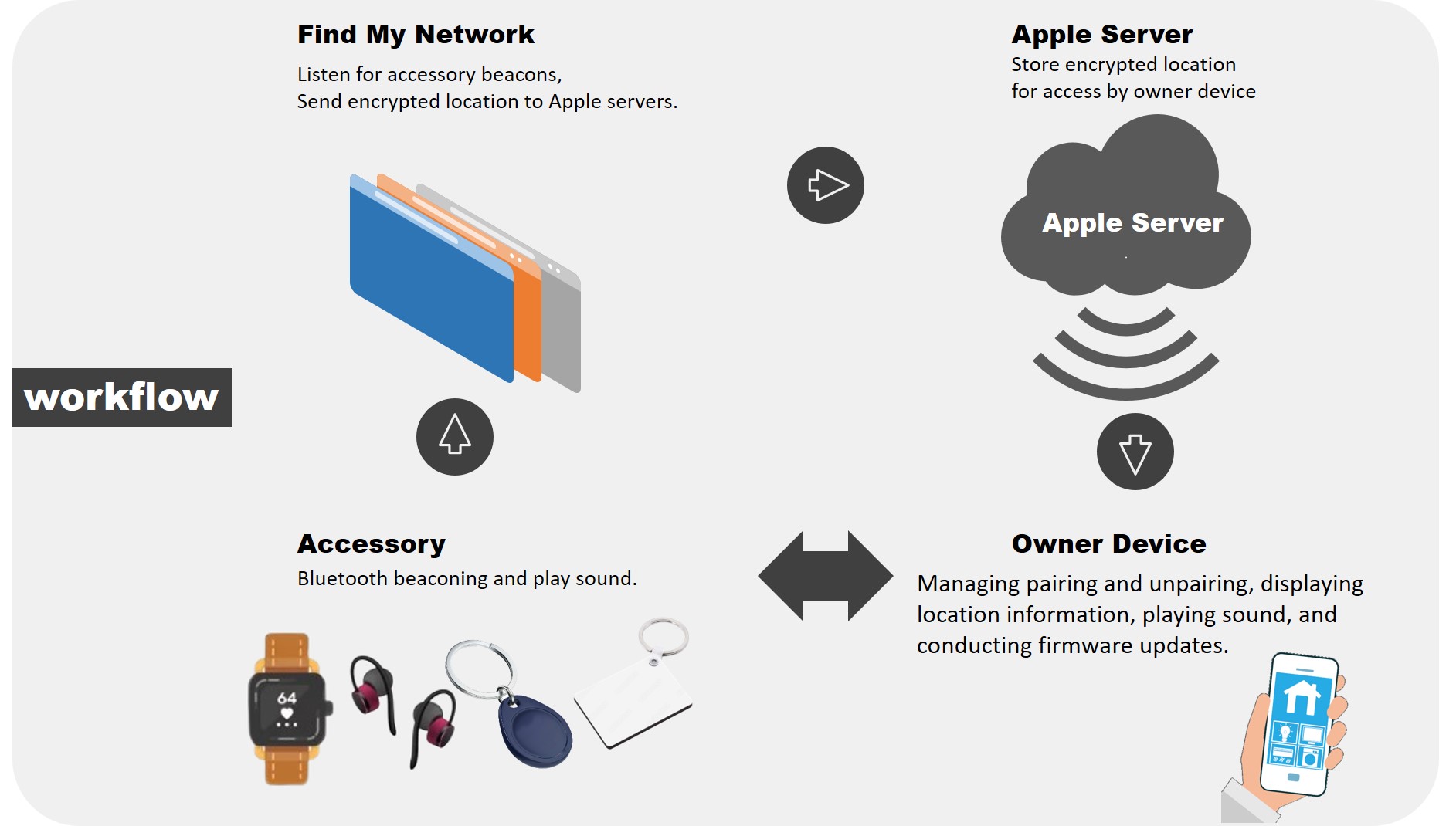
• After receiving the broadcast from the accessory, nearby Apple devices send the key and their own location information to the Apple server.
• The owner device retrieves the location information of the accessory from the Apple server through the Find My app.
• The more Apple devices there are near the accessory, the more accurate the positioning becomes.
• Lost Mode
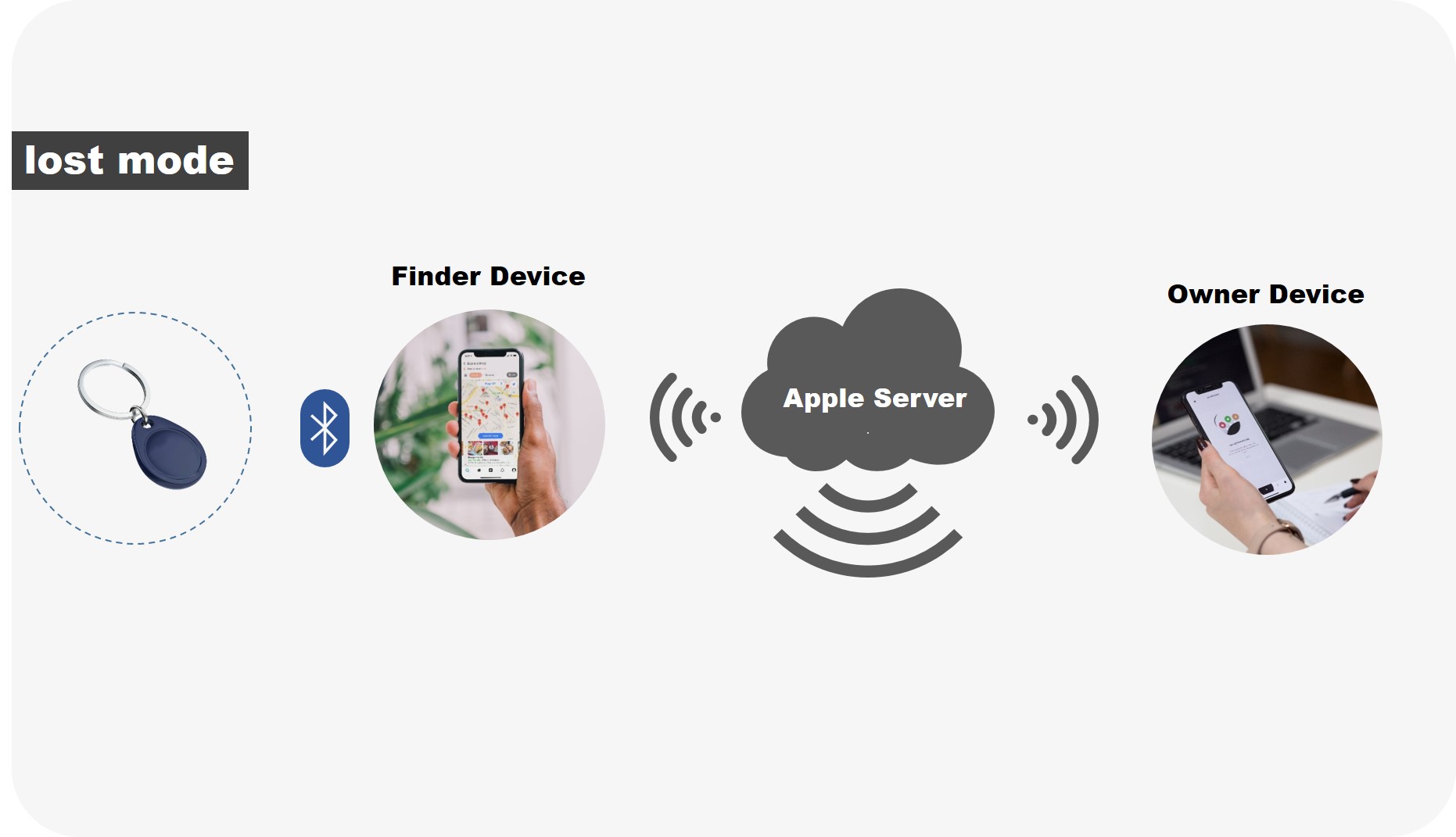
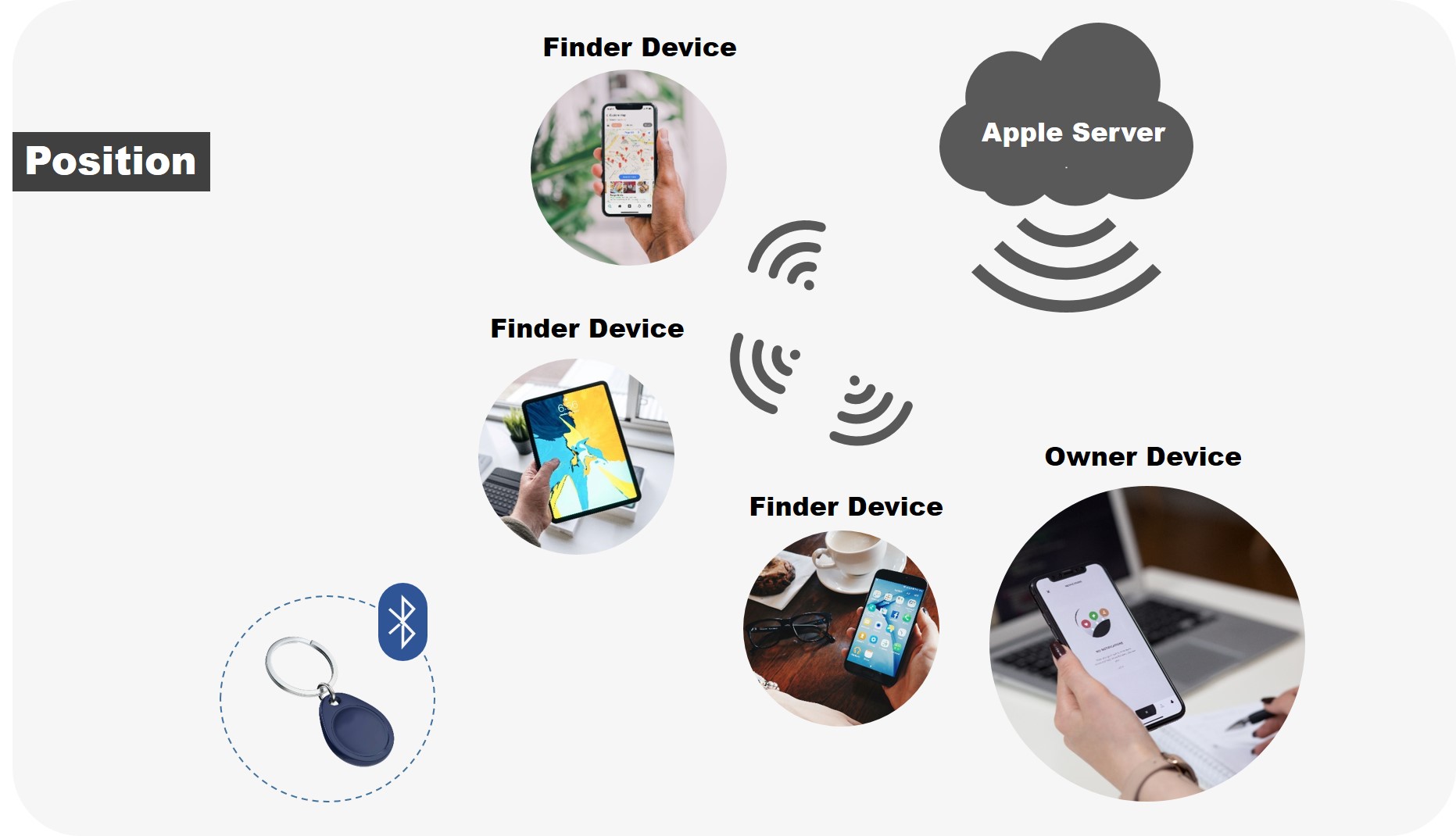
• The owner device can configure the accessory as "lost mode" in the Find My app, allowing them to set a contact phone number and message. The message content can be selected from a predefined list.
• If someone finds an unknown accessory, they can connect it to another Apple device and retrieve the contact information left by the owner, assisting in the recovery of the lost accessory.
• Once paired with the owner device, the accessory cannot be re-paired or used by anyone else, even if it is not set to lost mode.
• Unwanted tracking detection
• When an Apple device detects an unknown accessory continuously tracking its location, it will display a popup message to alert the user, notifying them that an unknown accessory is tracking them.
• Users can use the Find My app to make the unknown accessory emit a sound, helping them locate its position.
Find My Software State
The software state machine and transitions between states are illustrated in the following diagram:
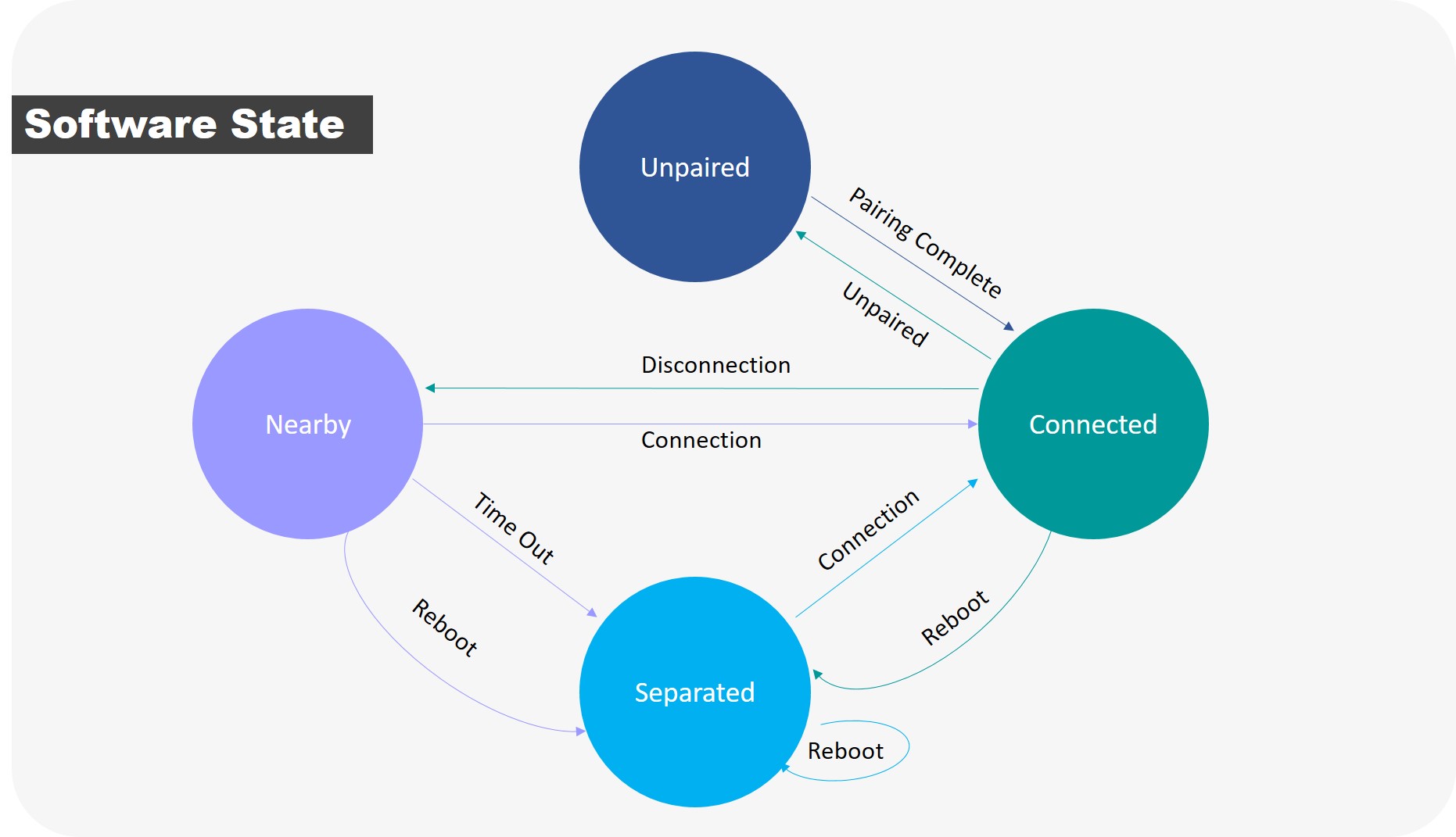
• Unpaired
⇒ Before being connected and paired by the user or after being unpaired, the accessory is in an unpaired state.
⇒ In this state, the accessory broadcasts at an interval of 30ms and continues broadcasting for a maximum of 10 minutes.
• Connected
⇒ After completing the pairing process, the accessory transitions from the nearby/separated state to this state upon being connected by the owner device.
⇒ Simultaneous connection is supported for two Apple devices under the same iCloud account.
⇒ Once pairing is completed, pairing with the Apple devices from other iCloud accounts is prohibited.
⇒ Disable motion detection.
⇒ Disable harmful tracking detection.
⇒ If the link encryption is not completed within 10 minutes, the accessory must disconnect from the BLE connection.
• Nearby
⇒ Immediately upon disconnecting from the owner device, the accessory enters this state.
⇒ Disable motion detection.
⇒ Disable harmful tracking detection.
⇒ The accessory broadcasts at an interval of either 30ms or 2s. The broadcast packet payload includes a portion of the primary public key and has a length of 8 bytes.
• Separated
⇒ The Nearby state times out (with a default timeout of 15 seconds) or the accessory has already been paired and reboots from the connected or nearby state, entering this state.
⇒ The accessory broadcasts at an interval of 2 seconds. The broadcast packet payload includes the primary or secondary public key and has a length of 31 bytes.
BLE Security
The Bluetooth address broadcasted by the accessory is set as the first 0 to 5 bytes of the public key, determined by the nearby or separated state and updated with state machine transitions. The accessory and owner device encrypt the BLE link using a long-term key (LTK) that is updated every 15 minutes, generating a new LTK through a key derivation algorithm. The design of updating the Bluetooth address and LTK using secure encryption algorithms significantly enhances BLE security, making it impossible to steal the exchanged BLE air packets even through Bluetooth protocol analyzers.
Find My solution based on Realtek BLE SoC
Realtek has implemented the Apple Find My solution based on the RTL8762 series BLE SoC, providing customers with Find My SDK/HDK for secondary development. Realtek has also collaborated extensively with two official Apple IDH partners and introduced several Find My products based on Realtek's solution.